Get started
Get started
The 51% attack on Bitcoin sometimes raises concerns in the community. These fears are not unfounded. Indeed, although no such attacks have occurred to date, we have already witnessed over 50% of computing power being controlled by the mining pool. Ghash.io in 2014.
Although the term “51% attack” is well known, its mechanism and consequences are often misunderstood. In this article, we offer you a simple and at the same time detailed explanation of what a 51% attack on Bitcoin involves. We look at how it works, its goals, its limitations, and strategies for preventing and responding to such a threat.
A 51% attack is a scenario in which a malicious actor or a coordinated group of malicious actors controls more than half of the Bitcoin network's mining power (hashrate). This situation presents a risk, as it allows the attacker to manipulate the blockchain by refusing to integrate the blocks of other miners. When a malicious actor finds himself in this situation and abuses his dominant position to carry out fraudulent actions, we then speak of a 51% attack.
The goals of a 51% attack on Bitcoin can vary, but they are generally motivated by profit or the desire to harm the system.
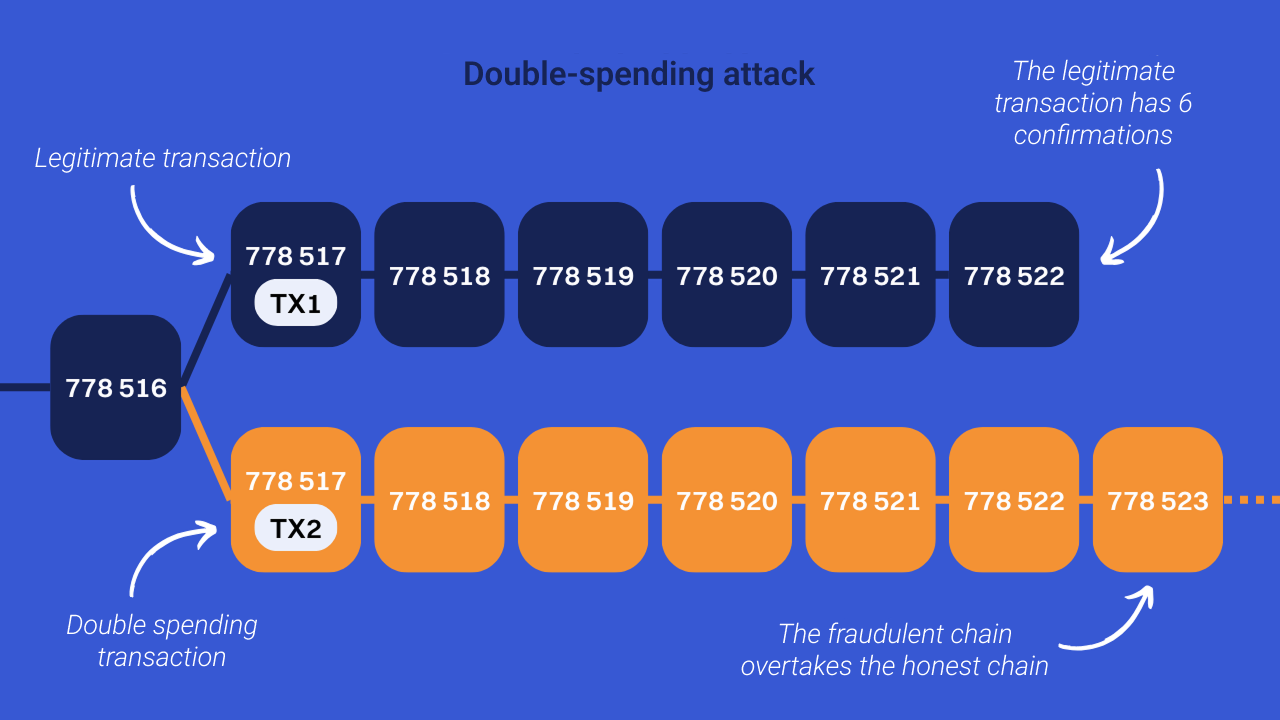
First, an attacker who controls more than half of the network's computing power is in a position to make what's called “double spending.” In other words, it can use the same piece of bitcoin (UTXO) in several different transactions, thus robbing recipients to get rich on the counterparties of these transactions.
To fully understand the double-spending process, let's take the example of an attacker going to a baker to buy a baguette in BTC. He completes a legitimate payment transaction and then gets his wand back.
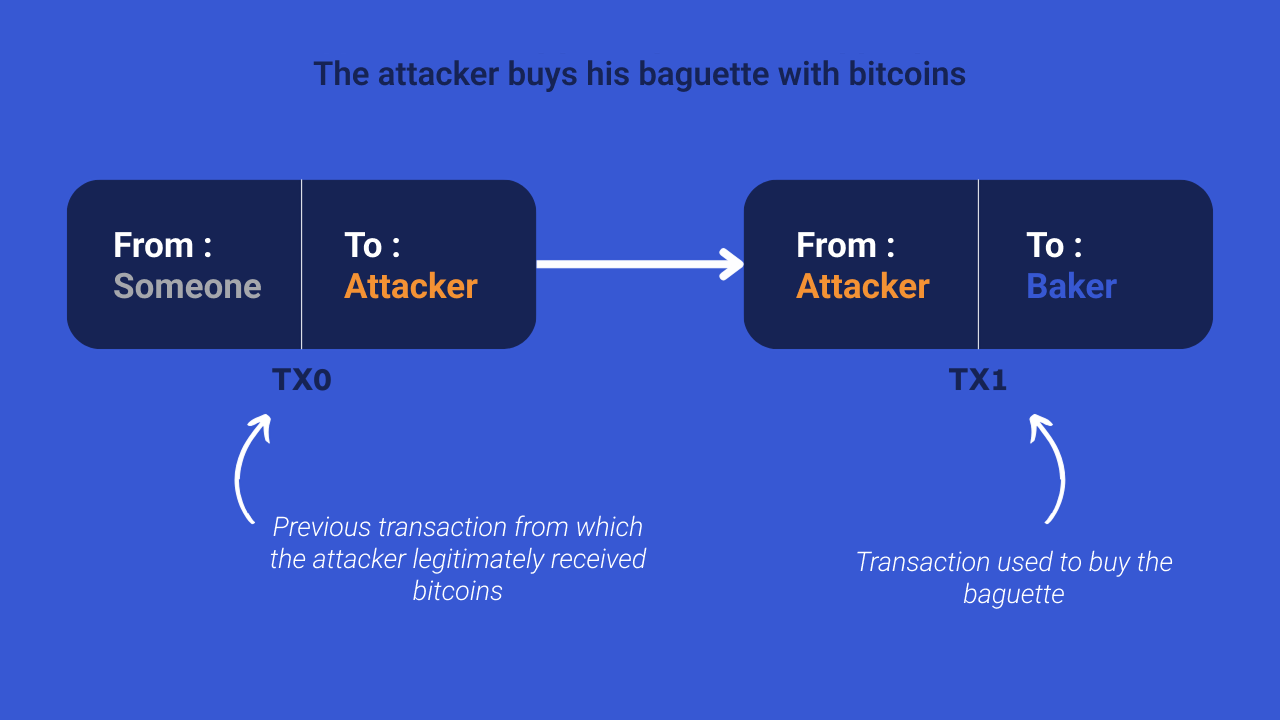
The attacker will then generate a second transaction, competing with the one used to buy the wand. This new transaction re-uses the same bitcoins, but this time sends them to a receiving address belonging to the attacker.
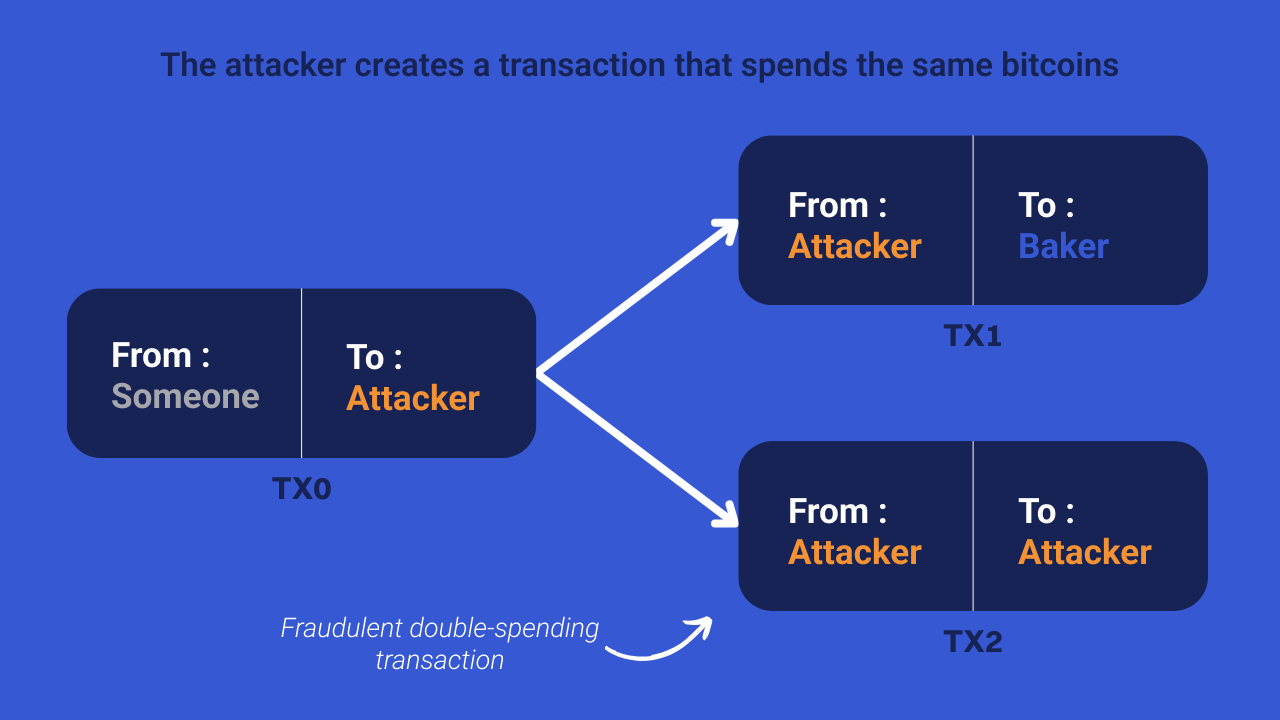
Normally, the initial transaction being the first one included in a block, the second (fraudulent) transaction should not be confirmed. To achieve his goals, the attacker will seek to cancel the block containing the legitimate transaction by mining his own block that includes the fraudulent transaction. So this will create two competing channels.
In order to make his chain containing the fraudulent transaction prevail, the attacker must mine new blocks on top of his own to overcome the honest chain and cause a reorganization of the nodes. This reorganization over several blocks is made possible thanks to the dominance of the attacker over the global hashrate. Thus, it can undermine a chain that can potentially surpass that produced by other miners. If this happens, the nodes will accept the fraudulent chain, as it represents the longest blockchain (with the most accumulated work).
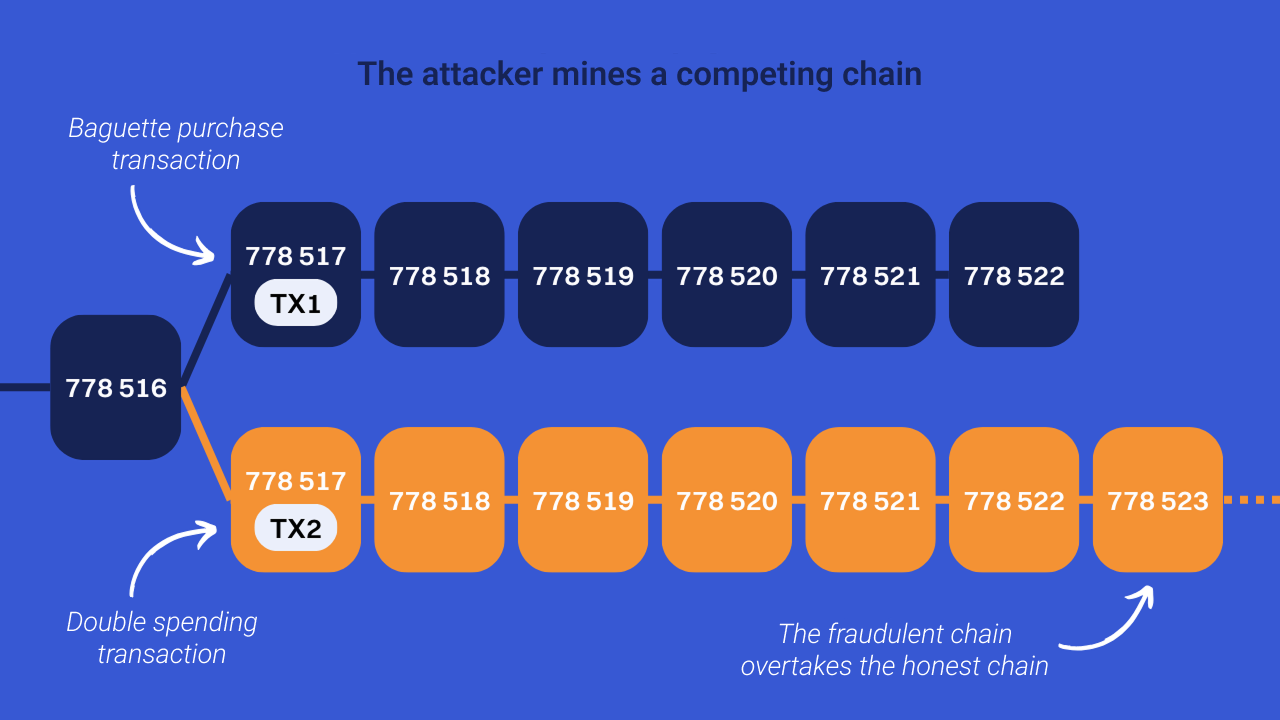
If this scenario succeeds, the attacker manages to recover the bitcoins spent on buying the baguette without having to return it to the baker. In short, he gets his wand for free (the wand and the money for the wand).
Apart from this double-spending operation, the attacker could also take advantage of his position with more than 50% of the hashrate to disrupt the normal functioning of Bitcoin by censoring transactions. Since he has the power to only accept blocks that he mines himself while having a chain with more accumulated work, he can arbitrarily decide not to include certain transactions in the blockchain.
It's important to understand that the risks associated with a 51% attack on Bitcoin are mostly limited to these two consequences: double spending and censorship. Contrary to popular belief, such an attack does not make it possible to irretrievably break Satoshi's innovation, to exceed the 21 million bitcoin limit by creating them ex nihilo, or to steal the bitcoins of other users. The impact of this attack concerns only future transactions and does not allow past transactions to be changed.
In the case of double spending, as we explained, the attacker can only act on his own transactions. So, in our example, the attacker could have recovered the bitcoins he spent at the baker, but only that transaction would be affected.
In addition, carrying out a 51% attack requires colossal computing power, making its cost prohibitive for most actors. These costs include the massive acquisition of specialized computers, called “ASICs” (Application-Specific Integrated Circuit), important energy sources, premises to house them, and a workforce to maintain them. Given the current hashrate on Bitcoin, such an attack, in addition to being extremely expensive, could encounter physical limitations, such as the production capacity of ASICs or the availability of energy on Earth.
Moreover, an attack by 51% is not a one-off act. To be effective, it must be maintained over time, due to the transaction confirmation process. Several confirmations (usually 6) are required for a transaction to be considered unchangeable. To make a double expenditure, the attacker must therefore maintain control over the majority of the computing power for a sufficient time to exceed the number of confirmations expected by the victims.
If the attacker's objective is censorship, they should maintain dominance for as long as they want to censor. As soon as it starts to falter, the competing blocks, which do not censor, can no longer be surpassed by the attacker.
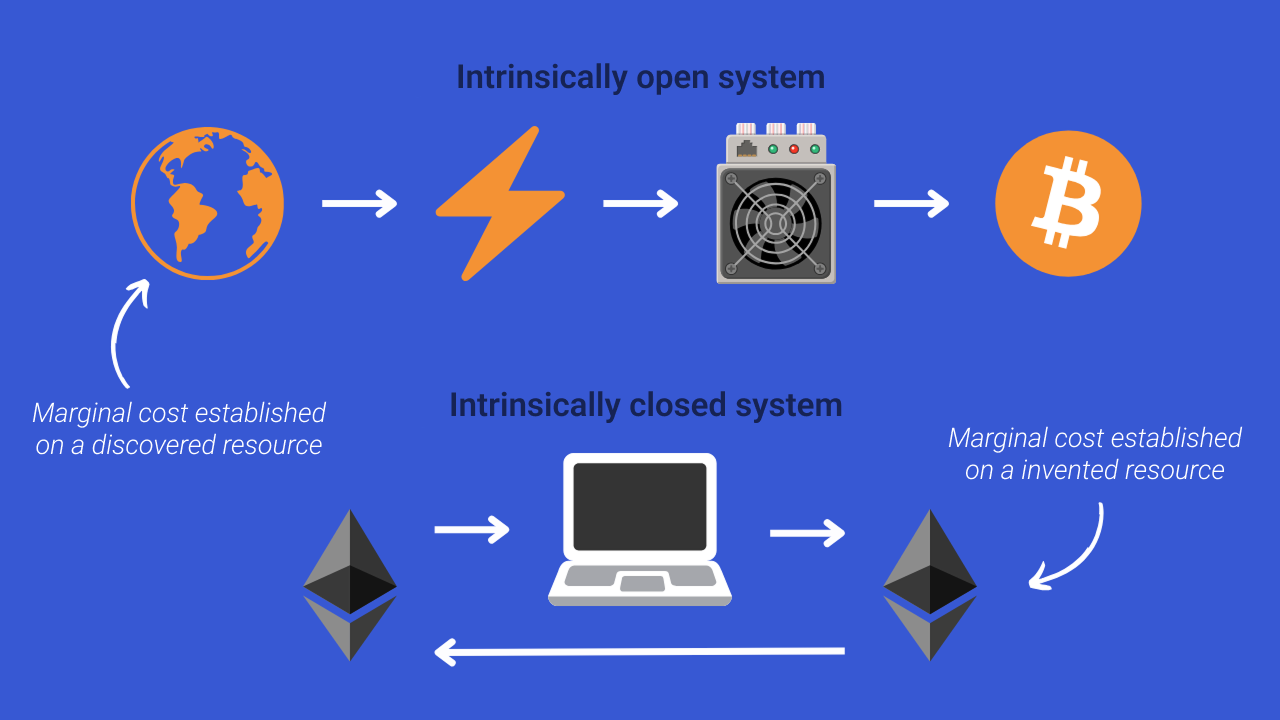
This additional difficulty in maintaining the attack over time is specific to cryptocurrencies operating on a proof-of-work consensus. In the case of a 51% attack on a proof-of-stake system (such as Ethereum), it is not possible to naturally dislodge the attacker, because the marginal cost of multiplying votes is established on the same resource as that granted as a reward for the production of blocks. However, it should be noted that proof of stake makes it possible to reduce the profitability of such an attack.
As you will have understood, a 51% attack on Bitcoin is easily detectable, complex and expensive to execute, for a relatively limited benefit for the attacker. According to game theory, it is economically much more profitable for a miner to participate honestly in the Bitcoin network than to attempt such an attack. By participating honestly, a miner receives bitcoin rewards for each validated block, which represents a steady and fairly predictable income. On the other hand, a 51% attack requires heavy investments in equipment and energy, but the attacker has no guarantee of benefits from this operation. In addition, the loss of trust resulting from the attack could cause the value of Bitcoin to fall, thus decreasing the value of possible rewards obtained by the attacker.
That is why it is extremely unlikely that a rational actor would undertake such an attack. However, if it were to occur and be maintained over time, several defense mechanisms exist to allow honest users to counter this attack.
➤ Learn more about how proof of work works.
Preventing a 51% attack on Bitcoin primarily involves increasing and decentralizing the computing power of the network. As we explained, such an attack requires controlling more than 50% of the mining power. To achieve this, the attacker therefore has 2 choices:
Decentralizing mining makes the first option more complex for the attacker. If a single major mining company owned 50% of the computing power, it would be relatively easy for an authority, such as the US government, to take control of that company. On the other hand, if the mining power is distributed among hundreds of companies in different countries, the task becomes significantly more complex. Decentralizing mining, across various companies, countries and individuals, is therefore an important preventive measure.
Second, increasing computing power makes the second option more difficult. The higher the hashrate, the more complex it is for an attacker to produce enough machines to surpass the existing hashrate.
Another important facet of prevention lies in educating Bitcoin users, as we are doing through the blog. Understanding Bitcoin. A user who keeps his bitcoins himself (self custody) and has his own full node is protected from undue manipulation and can choose the consensus rules that he wishes to support through his economic activity.
Although miners play a crucial role in the Bitcoin system, it is ultimately the users, through their economic activity, who hold the decision-making power. If an actor managed to sustainably maintain a 51% attack with the objective of censorship, it could naturally be dislodged by the market. Indeed, censored users, faced with the inability to see their transactions confirmed, will increase their transaction fees. This increase in fees works as a mechanism to counter censorship. This encourages honest miners to deploy a hashrate that is sufficient to confirm censored transactions and thus restore normal network functioning.
It would also be possible to make changes through a hard fork to reject the attacker's blocks. In the most extreme hypothesis, a change in the proof of work algorithm could even be considered to instantly neutralize the attacker, making all of his computing power obsolete. Its massive investment in mining machines would then become useless. Adopting such a solution would only be a temporary measure, far from ideal, since it would have the effect of reducing Bitcoin's security in the short term. But this simple threat by node operators in itself may be enough to deter a malicious actor from launching such an attack. This is a deterrent game similar to a UASF (User Activated Soft Fork), where the economic majority comes into play to support the usefulness of money.
➤ Learn more about the power games on Bitcoin.
The 51% attack is often overestimated on Bitcoin. Not only is it very complex to set up and maintain over time, but the potential benefits for the attacker are also low and uncertain. Indeed, if such a situation were to occur, it would not allow the attacker to steal bitcoins outside of his personal transactions, or to create coins from scratch.
This attack essentially allows two things: double spending (exclusively from a transaction that the attacker himself propagated) and the censorship of certain transactions. Moreover, this type of attack is quite easily detectable and there are many ways to counter it.
Although it is appropriate to work on the decentralization of computing power to prevent this type of attack, it should also not be brandished as a fatality that would destroy Bitcoin overnight.




