Get started
Get started

Because of its digital and open nature, the Bitcoin environment is regularly the scene of scams and hacking attempts. If you secure your funds in self-custody yourself, you may be the target of various thieves who will try to steal your bitcoins.
To reduce these risks of hacking and scamming, you should follow some tips for using Bitcoin. In this article, we explore best practices to follow to reduce these risks.
When you broadcast a transaction to the Bitcoin network, it is not immediately confirmed. You should wait for a minor to include it in a valid block so that she receives her first confirmation. Moreover, you have probably already heard from an informed bitcoiner that you have to wait for 6 confirmations for a Bitcoin transaction. Why is it important to wait for these confirmations to consider a transaction as validated?
The first confirmation of a transaction occurs when it is added to a block. Then, each new block built on top of the block with the transaction under study will constitute a new confirmation.

First of all, it is not recommended to consider a transaction as validated before it is even included in a block. This practice is called “zeroconf”. It remains risky since a transaction remains modifiable or replaceable by the sender while it is still in the mempool.
The mempool (Memory Pool) is a database, maintained independently by each node on the network, keeping Bitcoin transactions pending confirmation.

However, including a transaction in a valid block does not necessarily mean that it is unchangeable. Indeed, on Bitcoin, the irreversibility of transactions can only be probabilistic. Each new block mined on top of the one with your payment buries the transaction a bit more. That's why I prefer to talk about probabilistic irreversibility. Of course, it is always possible for a confirmed transaction to be ultimately unconfirmed, but this probability decreases rapidly with each additional confirmation.
➤ Learn more about Proof-of-Work mechanisms.
From the sixth confirmation for a transaction, the probability of it becoming unconfirmed again is so low that it can be considered zero. This is why we advise you to wait for 6 confirmations for important transactions.
All of this is due to the Bitcoin model. For a variety of reasons, a valid block is sometimes abandoned. This is what we call an expired block (“Stale block” in English). However, if your transaction is in a block that turns out to be out of date, then its status will change from confirmed to unconfirmed. Concretely, you thought that your transaction was included in a block, but since it is abandoned, your transaction can return to the mempool.
These outdated blocks are observed when the Bitcoin network divides. In English, this is called a “split” (not to be confused with a fork). When two miners find a valid block in a short period of time, then some nodes may have access to one block, and others will have access to the other block. Both blocks are valid, but they are at the same chain height. Afterwards, when a miner finds a valid block above one of the two blocks of the same height, the network will make consensus again on a single chain. One of the two blocks mined at the same height will be abandoned by the nodes. It's an expired block.
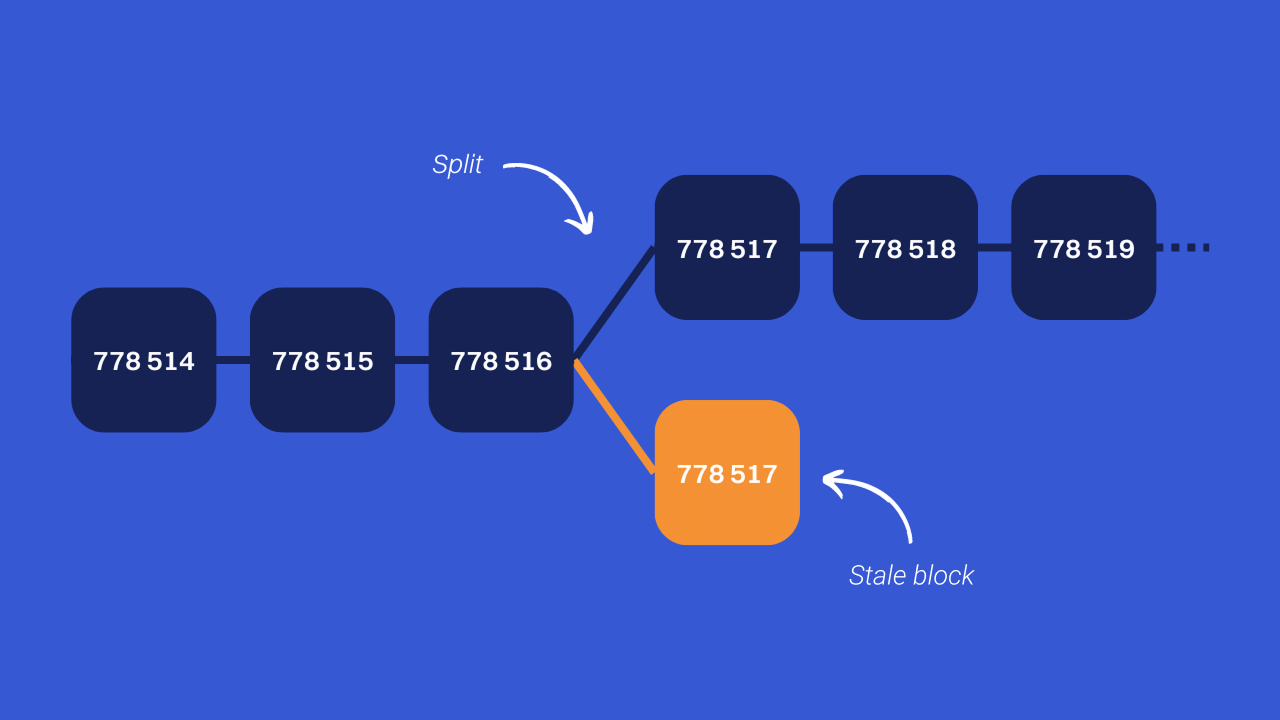
Outdated blocks are very often confused with orphan blocks. An orphan block separates itself from the chain since it does not have a parent block, unlike an outdated block, which separates because it does not have a child block. So these are two different concepts.
This process can happen naturally, in particular because of too much latency on the network, or be caused by certain surreptitious practices such as Selfish Mining. In all cases, the proof of work mechanism makes it possible to reduce this risk to a derisory probability by adding blocks on top of the one studied.
Obviously, it is necessary to adapt your level of control to the situation of the transaction. If the committed payment is made by a friend to your wallet, zeroconf may be sufficient. In fact, if there is any problem with the payment, you can always ask your friend to redo the transaction. This vigilance over confirmations should instead be carried out in risky situations, especially if you do not know the person with whom you are making a transaction. For example, if you sell your used car to a stranger, and the payment is made in bitcoin, you should not leave the keys until the payment has 6 confirmations.
In my article” 7 tips to improve the security of your Bitcoin wallet ”, I remind you of the importance of using a hardware wallet to store and manage the keys to your Bitcoin wallet. This type of device makes it possible to isolate the storage of your cryptographic keys in order to protect them from hacks. However, hackers do not necessarily need to have direct access to your keys to steal your bitcoins. That's what we're going to look at in this part.
When you use a dedicated device to store your private keys, you often have to use wallet management software in parallel (Ledger Live, Trezor Suite, Sparrow Wallet, Specter...) in parallel. This type of software doesn't store your private keys, but it does allow you to check your wallet balance, build unsigned transactions, and manage your wallet. However, this software is generally installed on a multi-purpose computer or on a smartphone, and these machines are necessarily more vulnerable to computer attacks. So, if you're using a hardware wallet, you shouldn't trust that software.
Blind signing consists of building a transaction to make a payment in bitcoin, and not verifying the transaction details on the hardware wallet before signing it. This is a dangerous practice since, in this case, the transaction is verified only on the computer screen. However, the PC software may be malicious, the display may be modified, or the verified transaction may be modified before it is sent to the hardware wallet.
The risk is therefore to sign a transaction that you believe to be another transaction. For example, the hacker can change the transaction amount to empty your wallet and change the destination address. This is what we call address “spooping.”
It is therefore essential to always check the details of a transaction (amount, destination address, fees...) on the hardware wallet screen in addition to the management software. Manufacturers of these machines often implement screens that are directly linked to the secure element of the device. So, when you check these details on the screen of your hardware wallet, you are convinced that the transaction you are about to sign contains the parameters you want.
.png)
In addition, you should also always check the validity of a receiving address on your hardware wallet before transmitting it to a sender.
➤ Discover our complete tutorial on using the Ledger Nano S Plus hardware wallet.
In the previous part, we saw that there are many risks around the software that is installed on a computer. A good practice that can greatly mitigate these risks is to always check the authenticity and integrity of the software you download, before installing it on your machine. This is valid for all types of software, and more particularly for those related to the use of Bitcoin.
To verify the authenticity of downloaded software, simply verify the legitimate developer's signature with GPG. To do this, you will need to have GPG on your computer. You can then verify the signature using the command line interface, or using specialized software such as Kleopatra.
To verify the integrity of a software, simply pass it through the designated hash function, and compare its fingerprint with that provided by the developer. This makes it possible to be sure that the software has not been modified to include malicious code. To do this, you can again use specialized software, or do it directly from the command line. For example, on Windows, simply open the command prompt, type the “Get-FileHash” command, and drag the executable to be checked.
.png)
These procedures may seem tedious to you, but in reality, they are quite simple and quick to perform. They allow you to ensure that you are in the process of installing legitimate software and that it has not been modified. In short, this allows you to avoid installing a virus or compromised software, and therefore to reduce the risks of hacking your bitcoins.
Bitcoin users are often the target of phishing attempts. It is important to remain vigilant in the face of these attacks.
Phishing is a technique used to attempt to steal a variety of personal information by coming into contact with the victim through various means. In the case of Bitcoin, it is generally the recovery phrase (24 words) that is targeted by thieves.
In most cases, these phishing attempts are burlesque and easily detectable. You may receive private messages on social networks or possibly texts or emails asking you to communicate your recovery phrase by various means. But sometimes these attacks are much more subtle and organized.
For example, in 2020, following the hacking of the database of a flagship of the crypto industry, some people who saw their mailing address leaked received fake hardware wallets at their homes. In this package, there was a letter falsely signed by the hand of the president of this company, explaining that it was urgent to use this new hardware wallet. Obviously, the fake material sent was in fact corrupt, and the victims who used it for their cryptocurrencies had their funds stolen.
The fight against phishing consists of two phases. First of all, it is necessary to limit your exposure on the Internet in order to prevent the risks of contact. If hackers don't have access to your personal data, they won't be able to contact you. If you use social networks, I strongly advise you to remain discreet about them when it comes to your use of Bitcoin. You should also be careful not to broadcast your personal contact information anywhere.
Then, you must always remain vigilant when contacted by any means to ask you to take any action. Thieves sometimes pretend to be famous people or someone close to you. They also often play on the concept of urgency, asking you to quickly take action, otherwise there would be serious consequences.
Obviously, I cannot describe here all the methods of operation used by these thieves since they are constantly evolving. It is therefore important to remain very vigilant when contacted by any means whatsoever (even by post).
In any case, keep in mind that it is usually your recovery phrase that is targeted. As a reminder, You should never communicate your 24-word sentence.
➤ Learn more about the mnemonic phrase for HD wallets.
More generally, it is important to maintain good digital hygiene. If you use a Bitcoin wallet on a compromised machine, it's possible that your funds could be blocked or hacked. Indeed, there are many possible attacks on a Bitcoin wallet, even on hardware wallets. Maintaining a healthy digital environment, with the use of a few best practices, allows you to limit these risks.
The basis of computer security is certainly password management. It is important to use strong and different passwords for each of your software and accounts. A strong password is the longest and most diverse suite possible. It must also come from a source that is as random as possible. So, I advise you to consult the table Hive Systems Password Table, which gives you an order of magnitude on how long it takes to brute-force your password.
A brute-force attack involves trying every possible combination for a password.
If the source of your passwords is not random enough, an attacker can easily crack them. You should therefore not use the name of your pet, a date of birth, a postal code or even one of your passions... It is also not recommended to have a password base and to use it in all its forms. For this purpose, the use of a password manager is often appropriate.
Moreover, the use of Bitcoin often involves the manipulation of wallet software and node implementations. It is important to keep these numerous tools up to date. Updates are frequently released to fix security holes or vulnerabilities that could be exploited to steal your bitcoins.
Of course, there are many other basic recommendations to follow to optimize the security of your digital devices. To find out more, I strongly advise you to consult these two CNIL resources, which deal with this subject more broadly:
This list of best practices to follow to avoid Bitcoin hacks and scams is of course not exhaustive. Thieves' techniques are constantly evolving as security systems are improved. It is therefore important to keep up to date with the evolution of best practices.
The risk of your bitcoin being stolen can never be completely eliminated. Even the best security systems can have flaws. The objective of securing bitcoins is to act so that the cost of an attack on your system is much higher than the potential gains.
To do this, you need to balance the risk between the risk of theft and the risk of losing your bitcoins. You should certainly be aware of the risk of theft and take action to reduce it, but without increasing the complexity of your portfolio unreasonably, otherwise you risk losing access to your bitcoins yourself.




