Get started
Get started

As Bitcoin democratizes, more and more people are choosing to secure their cryptographic keys themselves in order to regain possession of their funds. However, even the most motivated newbies can fall into pitfalls that can prove to be costly for the security of their bitcoins.
Here are 4 common mistakes to avoid to ensure the proper security of your Bitcoin wallet.
Some bitcoiners, after gaining some knowledge about Bitcoin, have the false good idea of imagining and applying their own cryptography to their wallet. For some, we can observe what is called the Dunning-Kruger effect. They overestimate their cryptographic skills and overlook the importance of standards.
It is important to clearly differentiate between security strategy and cryptography standards. You choose and model your security strategy based on various subjective elements. It must be based on cryptographic standards designed by real cryptographers, and controlled by their peers. Therefore, it is generally dangerous to change these standards yourself.
The most common example of this bad practice is the division of the mnemonic sentence. This consists of dividing a recovery sentence into three backups, one with the words 1 to 16, another with 8 to 24, and the last with the words 1 to 8 and 16 to 24. It is a practice that aims to eliminate the SPOF (“Single Point Of Failure” in English, “single point of failure” in French) that is the 24-word sentence. At first glance, this may seem like a good idea, but in reality, it is a very bad practice. This does not remove SPOF, and it greatly increases the risk of sentence theft by exponentially reducing its resistance to brute-force attacks.
➤ Learn more about the recovery phrase for Bitcoin wallets.
The border between your security strategy and cryptographic standards lies in the modification of the standard. If you do not change the standard, but adapt it to your situation, then your action falls under the security strategy. For example, you can choose to write down your recovery phrase on a paper medium, or on a metal support. In this case, the choice of support does not change the initial standard. On the other hand, if you choose to encrypt, encode, or split your recovery phrase, then you are inventing your own standard, and that can become dangerous.
I strongly advise you to respect the standards. There are a lot of proven options for designing a security strategy the way you want, and there will be even more in the future.
Privacy is not a mania for maximalist bitcoiners. This is an essential parameter that directly affects your personal security strategy. So, if you want to improve the security of your wallet, you should be interested in best practices for maintaining your privacy on Bitcoin.
To convince you, let me give you a telling example. If you constantly reuse the same receiving address to receive your purchases in DCA, then it is possible to make an undeniable link between your different coins. If one day, you use this address to pay for a good, the person who receives your payment will be able to know all the balance in your wallet. You can easily understand the risks that this involves, especially if you have a large amount of bitcoin.
Finally, this refers to the same practices that could be used with cash. When you go buy a baguette at a bakery in your neighborhood, you don't go there with a briefcase full of bills containing all your savings. No, you simply take a coin to pay for the wand. And of course Bitcoin, it's the same. If you use the same address again and again, an outside observer will be able to know all of your Bitcoin savings. In this example, the best practice would be not to reuse the same receiving address twice.
Also, despite their misleading names, never release your public keys, addresses, and extended keys publicly. Indeed, a person in possession of one of your public keys will be able to know their bitcoin balance and to trace your transactions. Again, this information can indirectly harm you. For example, if you have a large sum of bitcoins and you distribute the public key in question on your social networks, you risk suffering a malicious act. It is therefore advisable not to publish your reception addresses on your social networks, on the web and, more generally, on any public means of distribution. If you want to receive bitcoins in your wallet, give an address only to the person who should send them to you.
➤ Learn more about how Bitcoin works.
Obviously, there are plenty of other actions you can take to enforce your fundamental right to privacy on Bitcoin. I strongly advise you to take an interest in them in order to include them in your security strategy.
Creating a wallet is a particularly sensitive step in the security process. Most bitcoin losses come from bad practices at this stage.
First of all, it is important to back up your wallet using the recovery phrase. The latter must be written down legibly on a suitable medium. The words must be numbered and all kept on the same medium. This stage of scoring the recovery sentence should be done in a discreet environment, away from view and away from cameras.
Then, it is strongly recommended to perform a functionality test on this backup. Concretely, you will voluntarily delete your freshly created Bitcoin wallet, when it is still empty, in order to try to recover it exclusively from its sentence. This practice allows you not only to ensure the validity of your copy of the recovery phrase, but also to practice the recovery process, so you know how to respond in an emergency.
To really discover how to carry out this process, I advise you to read our Green Wallet installation tutorial.
Beyond the backup stage itself, it may be relevant to look at how the recovery phrase for your wallet is generated. It comes from a random number. If it is not random enough, it can reduce the security of your wallet. Thus, it is better to favor open-source wallets for which the process of generating the sentence has been verified by other people.
In addition, some wallets allow you the option of generating the random number at the base of your HD wallet yourself. This option is particularly interesting because it allows you to control the randomness of your sentence yourself.

When sending funds to your personal wallet, it is important to check the receiving address you are using before confirming. If you send your bitcoins to an address for which you do not have the private key, the bitcoin committed will be lost forever.
However, the receiving addresses on Bitcoin have a checksum. This cryptographic tool, included at the end of each address, allows software to detect and report a typo in the sequence of characters. Therefore, it is not necessary to check each character one by one across the entire address. A simple check of the last few characters of the address (which corresponds to the checksum) is in theory sufficient to ensure that we did not make a mistake. Checking the validity of this checksum also ensures that no malicious software has changed your address before confirming the shipment.
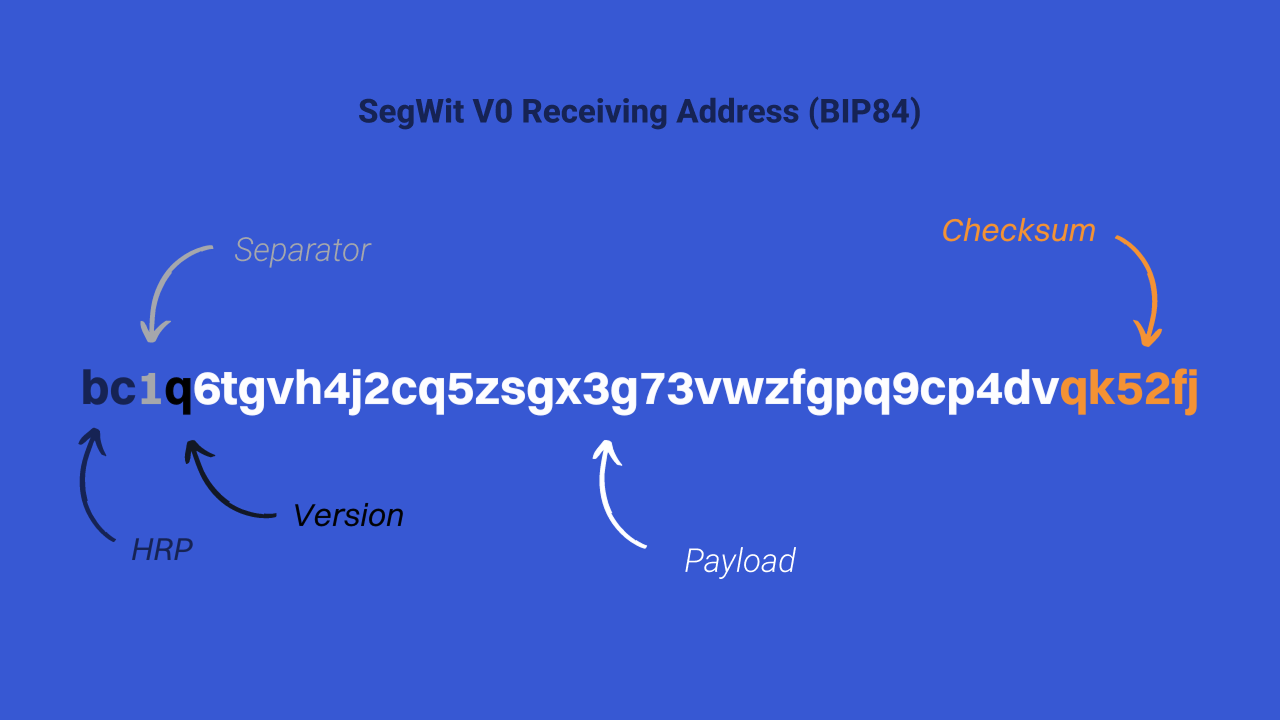
Attention, this type of device (the checksum) does not exist on a public key. If you use public keys to block bitcoins, with a P2PK script, you should check each character of the key one by one.
If Bitcoin self-custody is a new concept for you, it is important that you avoid these few mistakes in order to ensure that your funds are secure.
📌 Here are the key takeaways from this article:




