Get started
Get started

November 14 marked the second anniversary of the activation of the “Taproot” Bitcoin update. Like SegWit, Taproot is one of the protocol's major soft forks, those that only happen once every three or four years. Even today, the subtleties of this technical modification are sometimes unknown. To enlighten you on the ins and outs of Taproot and to understand why this update was important for Bitcoin, we offer you a simple explanation in this article.
Taproot is a major update to the Bitcoin protocol that brings new functionalities. It is a soft fork, which means that the new rules put in place are backwards compatible with the old ones. This update was locked at block 687,284, on June 12, 2021, when 90% of the blocks generated during a period sent a favorable signal, thus showing the readiness of miners to activate the Taproot update.
Activation finally took place at block 709 632 on November 14, 2021, almost four years after the first discussions on this subject between Pieter Wuille, Andrew Poelstra and Gregory Maxwell on this subject. This was the first major upgrade attempt since the thorny activation of SegWit in 2017, which led to conflicts in the community.
Taproot is a kind of package that includes various modifications for Bitcoin. The update includes the BIP 340, the BIP 341, and the BIP 342. Let's discover all these new features together.
📌 A “BEEP” for” Bitcoin Improvement Proposal ” is a formal process for proposing a modification of Bitcoin.
The first major innovation introduced by Taproot lies in the implementation of a new signature algorithm based on the Schnorr protocol.
As mentioned in our previous articles, bitcoins are materialized on the blockchain in the form of UTXos. They are essentially larger or smaller pieces of bitcoin. These UTXOs are protected by conditions that specify how they can be unlocked. An electronic signature algorithm is generally used to establish these conditions. Thus, to spend the bitcoins in your wallet, you must provide a signature with the private key associated with the public key that was used to lock your UTXos.
When creating Bitcoin, Satoshi Nakamoto chose to use the ECDSA electronic signature algorithm (Elliptic Curve Digital Signature Algorithm). This algorithm works very well, and it is still used today, but Schnorr is still more efficient on some technical points.
It's unclear why Satoshi chose ECDSA over Schnorr when launching Bitcoin. A hypothesis often raised is that the Claus-Peter Schnorr protocol was under patent until February 2008. Although Bitcoin came into being only a year later, in January 2009, no open-source standardization for Schnorr signatures was then available.
The Taproot update now offers us the possibility of using this type of signature. Compared to the ECDSA algorithm, Schnorr has two main advantages: its signatures are Lineares and more lightweight.
The linearity property allows multiple public keys to be aggregated into a single key. Thus, a multi-signature script can be condensed into a single key, acting much like a summary of all the other keys involved in multisig.
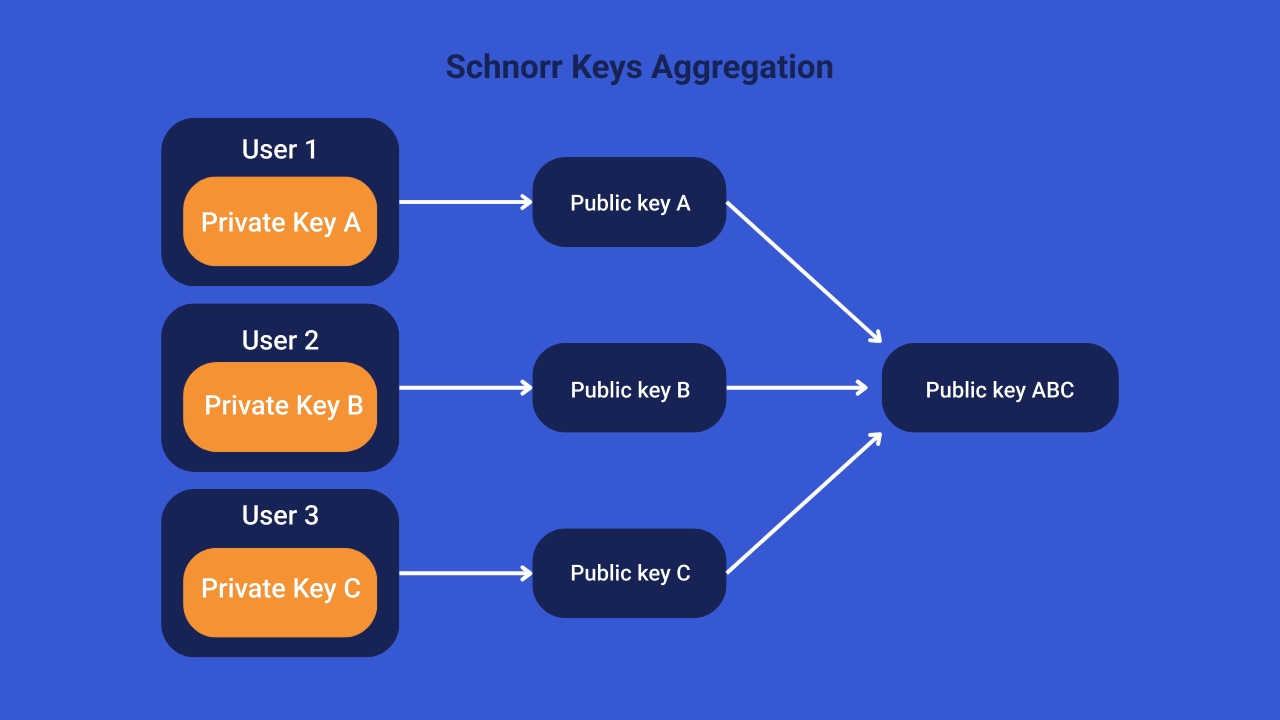
This public key, which actually embodies a set of other public keys, can be used to secure bitcoins. Similarly, it is possible to aggregate the signatures from the multisig in order to create a unique signature, allowing the public key to be unlocked.
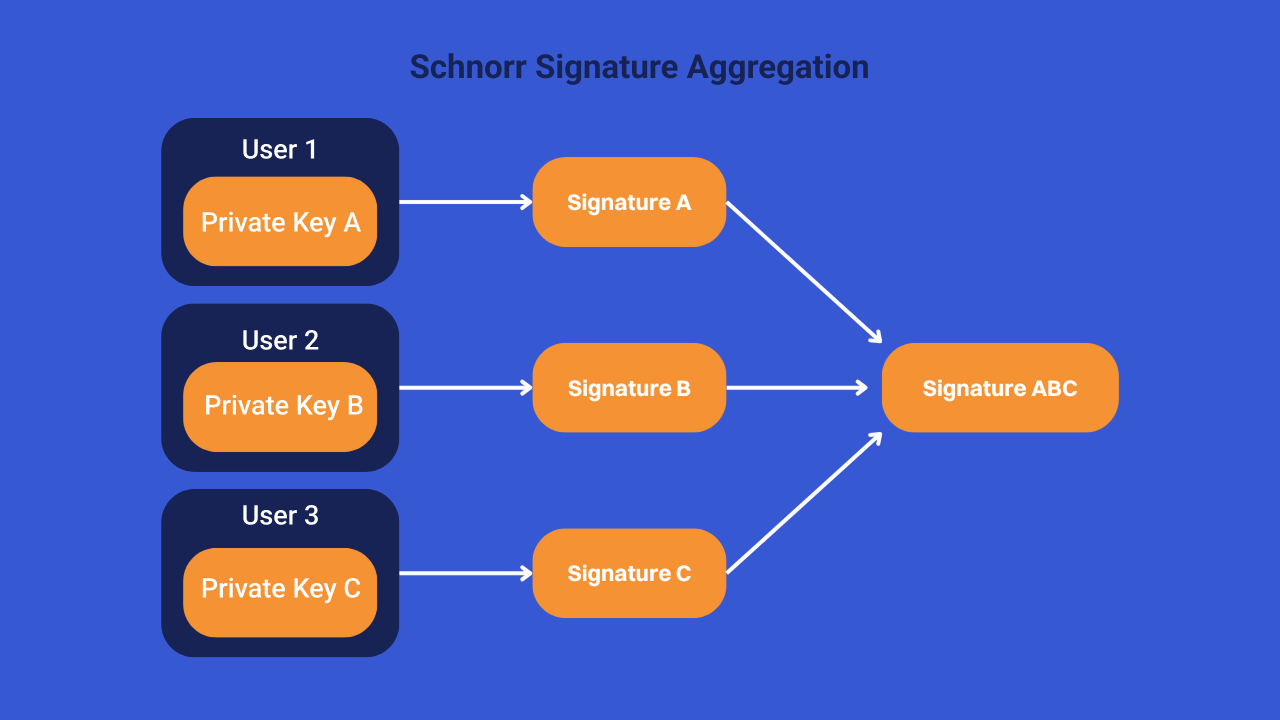
This linearity of Schnorr signatures has the advantage of minimizing transaction fees for multi-signature wallets, while increasing their confidentiality. Indeed, the latter become indistinguishable from other transactions on the blockchain. In fact, the Lightning Network uses multi-signature scripts to establish payment channels. Schnorr therefore makes it possible to reduce costs and make the opening and closing of Lightning channels indistinguishable. In addition, this aggregation of signatures establishes a form of plausible denial for all Taproot transactions on Bitcoin. It is becoming impossible to determine whether a specific UTXO is owned by a single person or by several. Finally, linearity also has the advantage of reducing the number of calculations performed by the nodes that verify the validity of transactions.
Beyond these linearity benefits, Schnorr signatures are also lighter than ECDSA signatures. From a technical point of view, Schnorr's signatures are provably secure and are by nature non-malleable.
ECDSA and the Schnorr protocol fall under the same category of cryptographic algorithms, known as “cryptography on elliptic curves.” They use exactly the same elliptical curve in the context of Bitcoin, called “secp256k1”.
Taproot also introduced the BIP 341, which aptly gives this soft fork its name. This update introduces a new way to block bitcoin. These new transaction outputs are called “SegWit V1" or “P2TR (Pay-to-Taproot).”
Bitcoins secured by a P2TR script can be released in two ways:
In other words, we can perfectly block our bitcoins as we did before with a simple private key that allows them to be spent. But if we wish, we can also define additional possibilities that will also allow us to unlock our bitcoins.
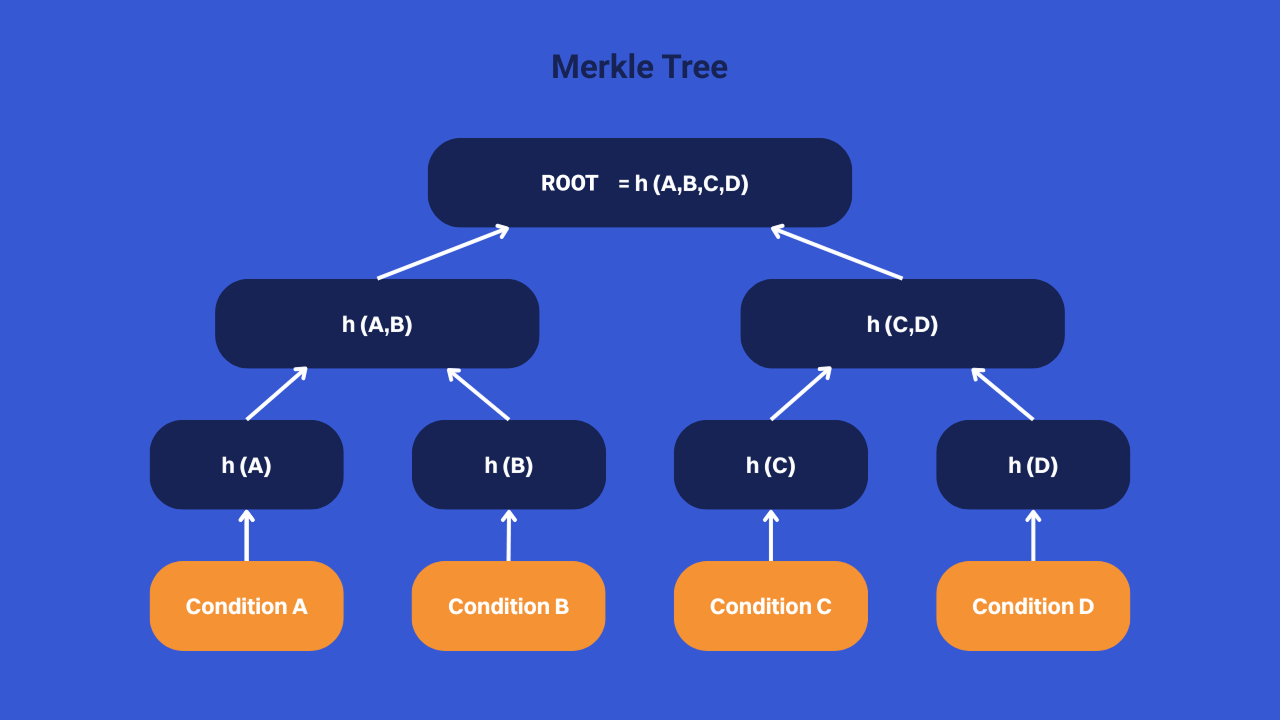
For example, you could set up four specific conditions, which we'll call A, B, C and D, each of which allows you to unlock your bitcoins. These conditions would be incorporated into a Merkle tree. It is simply a data structure for verifying the inclusion of a particular piece of information within a larger set.
To do this, the conditions A, B, C and D are passed into a hash function, thus generating H (A), H (B), h (C) and H (D). These hashed values are then grouped and hashed again in pairs, until a unique hash is obtained, which is called “Merkle root”.
This Merkle root, which is referred to as M, is assimilated to a public key. It is then combined with the master key P, which allows a classic expenditure, to form a new public key called Q. This aggregation of keys is precisely made possible by the linearity of Schnorr signatures.
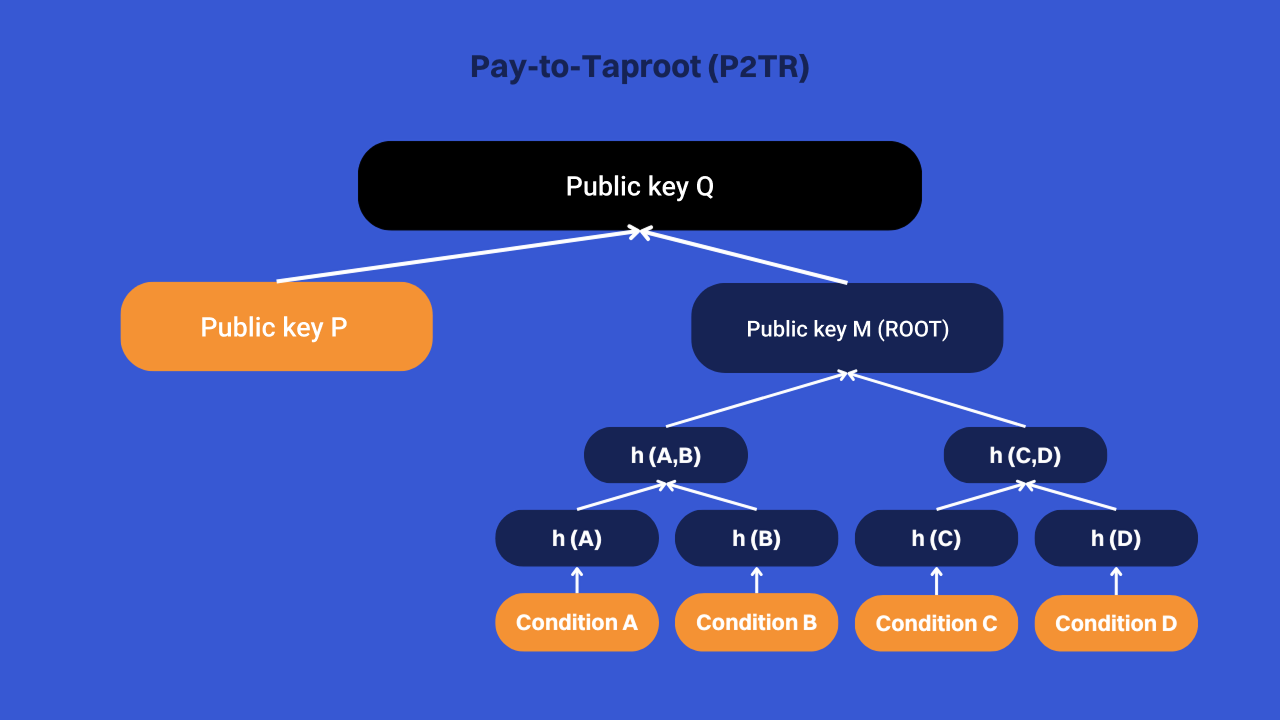
To release the bitcoins locked on the public key Q, you have two options:
When spending, only the condition used is revealed. Thanks to the Merkle tree structure, nodes can check the validity of the condition without having access to all the other conditions. For example, if you use the condition B to spend the bitcoins, then A, C and D remain hidden.
The advantage of this P2TR security method lies in the possibility of configuring complex scripts without having to expose them publicly on the blockchain. This promotes both user privacy and the scaling up of smart contracts developed within the Bitcoin network.
Finally, the last BIP introduced with Taproot is called Tapscript. The purpose of this update is to modify some opcodes of the classic Bitcoin scripting language, in order to define the new scripting language used for Taproot expenses.
The scripting language is the mechanism that allows the addition of spending conditions on UTXOs. So when you receive bitcoin at a designated receiving address” A ”, these are protected by a script stipulating that:” To spend these bitcoins, an electronic signature corresponding to the public key associated with address A must be provided ”. To write these scripts, specific commands known as opcodes are used.
In order to implement the various changes associated with Taproot that we mentioned in the previous parts, it was necessary to revisit the scripting language. This is the purpose of BIP 342, which deactivates or modifies certain opcodes, and adds new ones.
➤ Find out who controls the Bitcoin protocol.
Taproot represents a major evolution of the Bitcoin protocol, activated in November 2021 through a soft fork. This update includes the implementation of three distinct BIPs:
To sum up, Taproot offers considerable benefits in terms of privacy, flexibility, and scalability, especially for smart contracts and complex scripts on Bitcoin. It is an essential technical prerequisite for improving Bitcoin's second layers, such as the Lightning Network, as well as for developing innovative new protocols.
➤ Understand the difference between a soft fork and a hard fork on Bitcoin.




