Get started
Get started

In the previous article, we saw that the real use of Bitcoin can only be done when the user manages the storage of his own keys himself. So there are various tools that allow you to create keys, keep them, and use them to sign a transaction. These are Bitcoin wallets.
In this article, we look at the various solutions that exist for storing keys. We will see what are the characteristics of these portfolio supports, who they are intended for, and what are the associated risks. We also talk about different portfolio structures, and key derivation options.
The first category of wallets consists of those that are commonly referred to as “hot wallets” or software wallets. Concretely, they are specialized software that you can install on a versatile electronic device. They are either mobile applications or computer software.
When using a software wallet, your private keys are stored directly on the device in question. There is therefore a risk of hacking if the machine used is compromised. Indeed, the more versatile a device is, the more it has a large attack surface, and thus potentially numerous attack vectors. However, there are numerous ways to improve the security of a software wallet. For example, one of the most relevant is the use of a passphrase.
A passphrase is an additional and optional password added to the Bitcoin wallet at the seed level.
➤ Learn more about the BIP39 passphrase.
This type of wallet is therefore not the most secure, but it still has some advantages:
There are therefore mainly two situations in which the use of a hot wallet is relevant. First of all, if you need a mobile wallet that is quickly accessible, then you can keep a small part of your savings on this type of wallet. Then, if your Bitcoin savings are too low to justify the purchase of a hardware wallet, in this case the software wallet is a good compromise for you.
For example, if you are a novice and have a small savings in bitcoin equivalent to €100, buying a hardware wallet, which generally costs at least €70, is irrelevant. Using a hot wallet will be more suitable for you.
Here are some examples of free and open-source software wallets:
“Open-source” means that the computer code that makes the software work is freely distributed and accessible by anyone. Open-source software has advantages in terms of security and transparency compared to proprietary (closed-source) software. They can be reviewed by a large user community, allowing for better detection of security breaches.
Hardware wallets, sometimes called “cold wallets”, “signature devices” or even “hardware wallets”, are again software. On the other hand, unlike hot wallets, they are installed on a dedicated machine, not connected to the Internet and often specialized.
These wallets come in various forms depending on the brand chosen. Some look like a USB stick, others like a small calculator, and some even look like smartphones.
When you use a hardware wallet, your private keys giving access to your bitcoins are kept on it. Since it is a device dedicated only to this use and not connected to the Internet, it has an extremely low attack surface. As the attack surface is smaller, there are fewer potential attack vectors, and therefore your bitcoins are more secure.
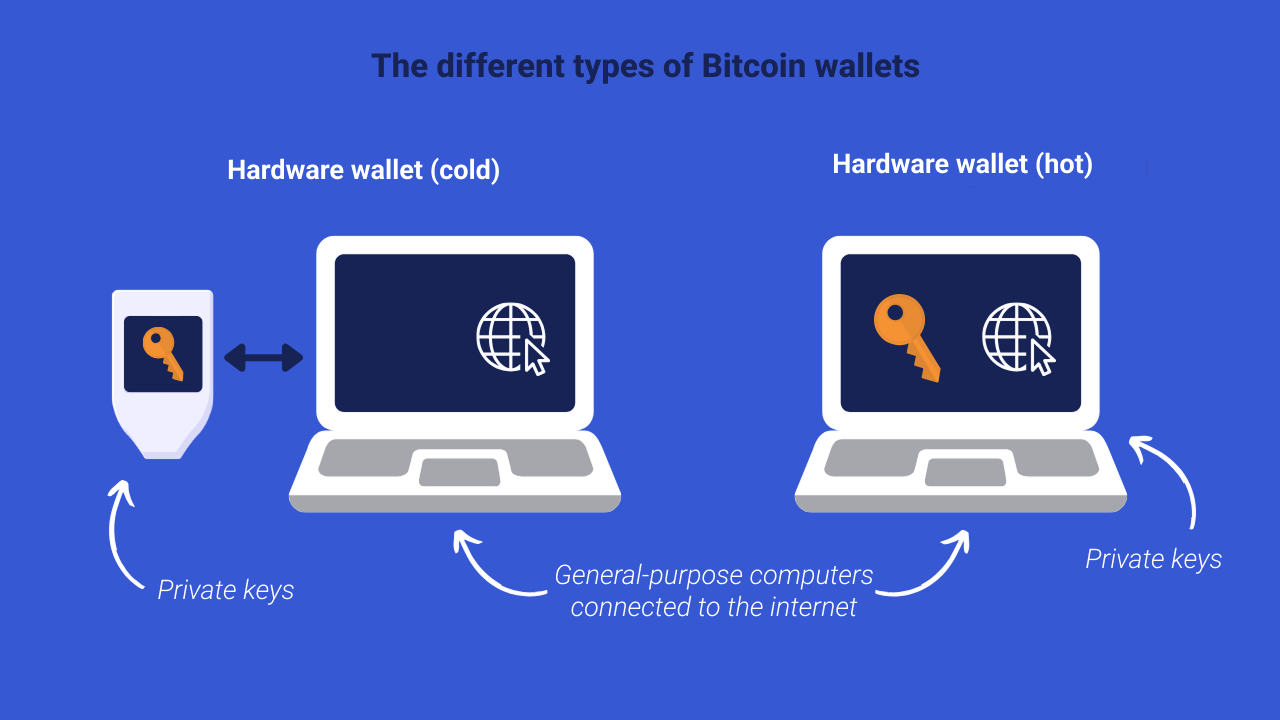
This category of Bitcoin wallet supports therefore has the advantage of being more secure, but it still has some disadvantages:
The hardware wallet is then preferred to secure large amounts of bitcoin. It is particularly useful for storing your long-term savings.
Here are some examples of hardware wallets:
However, it should be noted that these categories of “cold” and “hot” wallets remain subjective estimates subject to debate. The same wallet support may be considered by some as a “hot wallet” and by others as a “cold wallet”. The border between the two is bound to be quite fluid. It is therefore much more relevant to study each solution individually, presenting its advantages and disadvantages compared to the others, rather than categorizing each portfolio support by default.
Since Bitcoin ownership is simply achieved through knowledge of cryptographic keys, there are plenty of other options for storing them.
For example, some use what is called a “paper wallet.” They will simply write down their private key on a piece of paper in order to keep their bitcoins. This archaic technique is obviously very risky since the paper in question constitutes an SPOF (Single Point Of Failure = single point of failure). If it degrades or is stolen, the user loses his bitcoins.
The advantage of this type of wallet is that the key is kept outside of any computer system. Its attack surface is therefore reduced to physical attacks. Its disadvantages include the following:
It is also possible to remember only the information that allows access to the keys. These are called “brain wallets”. Of course, I strongly advise you not to carry out this type of practice. By default, when securing bitcoins, you shouldn't trust your own memory. In addition, setting up this type of wallet often requires the use of information that is not very random, in order to be sure to remember it, and this increases the risk of a brute-force attack.
On the other hand, among hot wallets, there are other sub-categories of wallets. For example, there are wallets in the form of browser extensions. In general, I don't recommend these types of wallets because they're not very useful, and they excessively increase the attack surface.
In fact, the comparisons in this article refer to the different types of portfolio supports. In other words, the main categories of machines and software that can host a Bitcoin wallet are studied above. However, the wallet itself, regardless of its support, can take different forms. There are several, which differ in their management of cryptographic key pairs.
As we saw in the article introducing the concepts of autonomous custody, UTXOs (bitcoin coins) are blocked by spending conditions. These conditions are freely set by the user. It is therefore possible to manage your key pairs in a non-standard way. Nevertheless, most users prefer to choose well-defined categories.
The best known includes deterministic and hierarchical wallets (“HD wallets” in English). They derive key pairs deterministically from the unique information at the base of the key pairs, and there is a hierarchy between the keys. This initial information serves as a backup for all other keys. Today, this category is the one preferred by users. By default, everyone uses an HD wallet.

➤ Learn more about the HD wallet recovery phrase.
However, there are other types of wallets. Among the oldest, we can mention wallets such as JBOK (“Just a Bunch Of Keys” in English) which are simply an agglomeration of random keys, independent of each other. There are also variants of portfolios that are deterministic, but not hierarchical.

In general, the HD wallet is still the category recommended to the user. It offers a good compromise between practicality and security, both for a beginner user and for an experienced user.
The two main categories of Bitcoin wallet holders are software wallets, also called “hot wallets”, and hardware wallets, also called “cold wallets.” Each has its pros and cons. The same user often has a cold wallet to secure their long-term savings, and a hot wallet for their daily transactions.
If you are just starting out learning about Bitcoin, and have few funds, it may be worth starting slowly with a simple software wallet. You will be able to get started, understand the essential functions of the Bitcoin wallet and test the recovery. You will be more serene with self-custody and you can later switch to a more secure hardware wallet.
As for the wallet itself, it is generally advisable to use a deterministic and hierarchical wallet. This type of wallet specifies that the keys blocking the user's bitcoins are all generated from unique and random information.
In terms of securing cryptographic keys, there is always a compromise between dealing with the risk of theft and dealing with the risk of loss. In general, the more you increase the security of your wallet, the more you increase its complexity, and therefore the risk of losing access to your keys yourself. Thus, it is important to know how to place the balance between security and simplicity, considering your personal environment and your own assessment of existing risks.
Finally, it is crucial to understand that zero risk does not exist in computer security. With the adoption of best practices, you can reduce the risk of having your bitcoins stolen, but it is impossible to annihilate it. Thus, there is no ultimate security that allows zero risk.




